Phishing Scam Hits Aave a Day After $60B Milestone
Just a day after celebrating $60 billion in total value locked (TVL), the leading DeFi platform Aave faced a phishing attack that drained funds from user wallets.
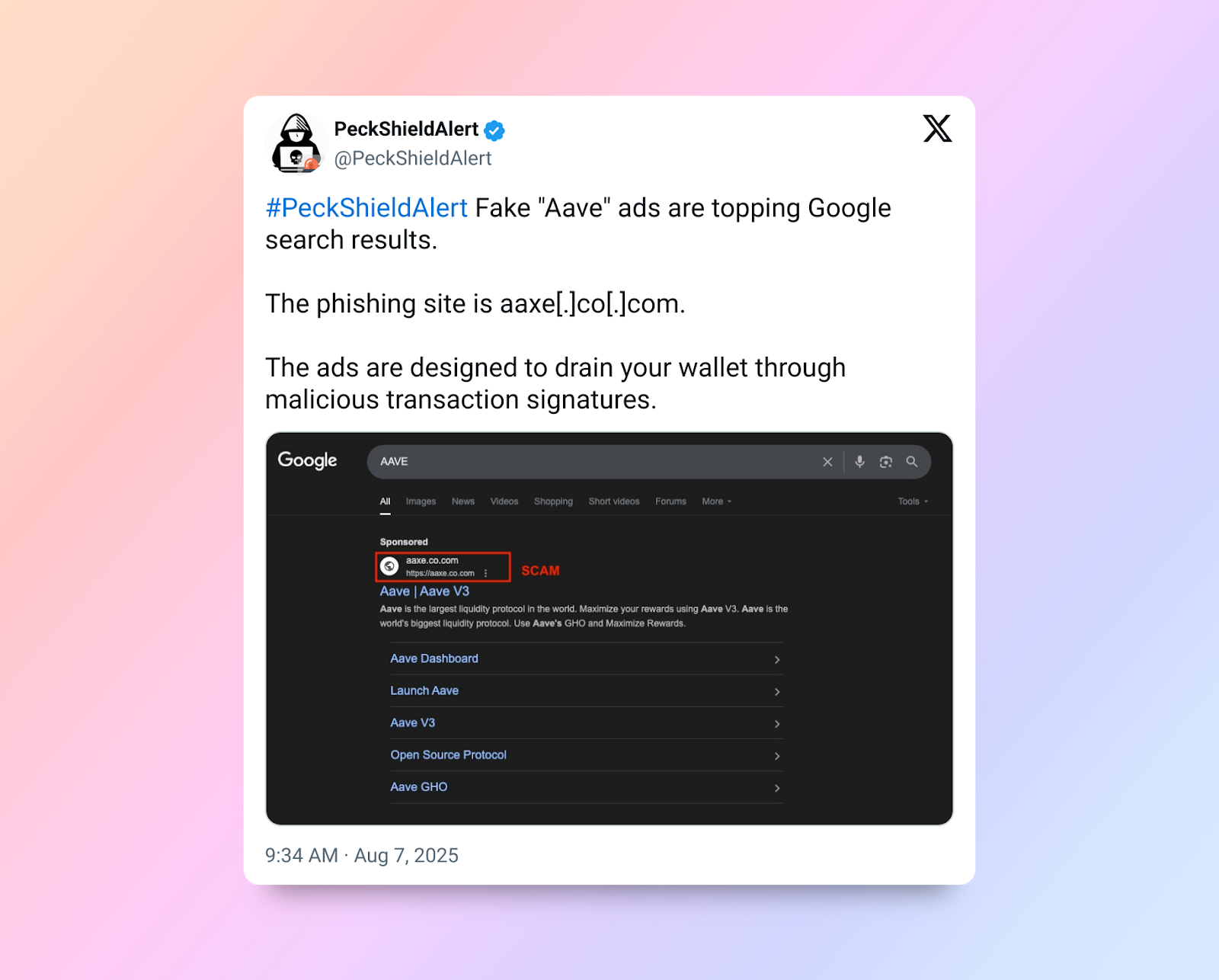
In this case, scammers launched the attack through a malicious front-end designed to look like Aave’s official app. Consequently, users who visited the spoofed site connected their wallets and signed approvals, unknowingly authorizing a smart contract that stole their assets.
Meanwhile, on-chain analysts continue to review the total damage. Several victims have already confirmed missing funds, and investigators have traced the losses to lookalike domains. Because these domains and the fake interface closely mirrored the real Aave dApp, victims believed they were interacting with the legitimate platform — a tactic frequently used in phishing scams.
Importantly, this attack came just after Aave’s $60B TVL milestone, making the timing even more alarming. As Aave climbed to the top ranks of DeFi protocols, it simultaneously attracted more attention from determined bad actors.
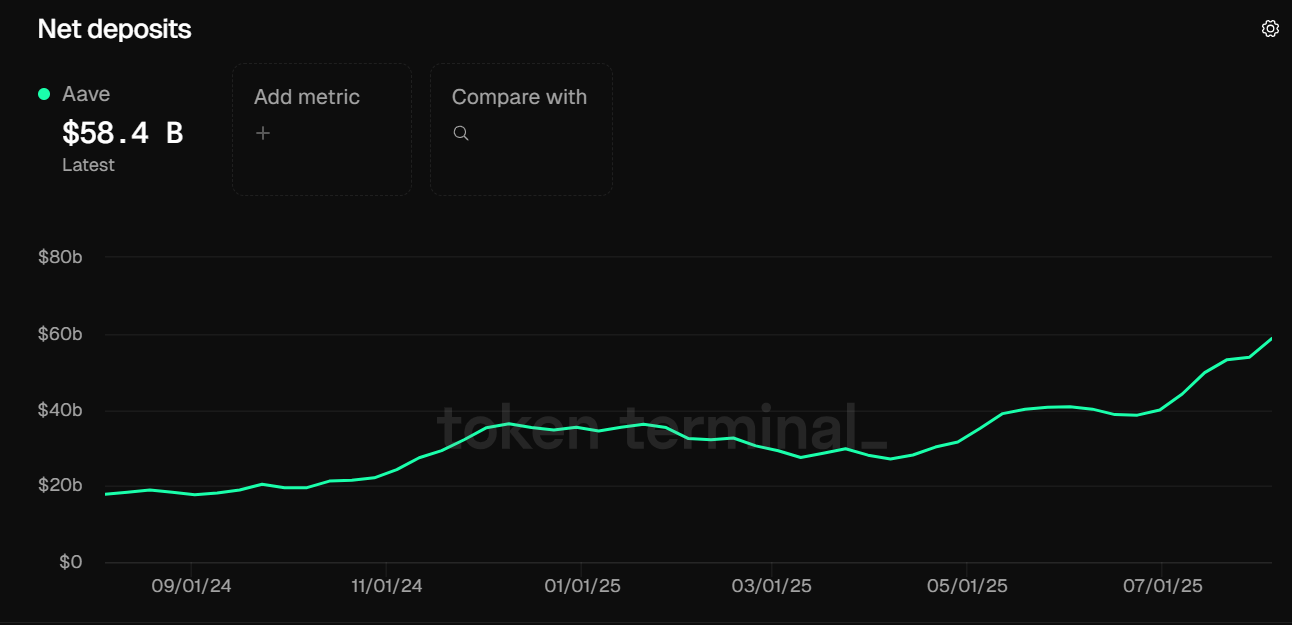 Net deposits in Aave across all chains.
Net deposits in Aave across all chains.
How Chain Retrieval Tools Can Prevent These Attacks
Ultimately, this incident highlights why chain retrieval is now an essential defense for crypto users.
In simple terms, chain retrieval refers to using smart tools to monitor, trace, and analyze wallet activity and smart contract behavior on-chain. Therefore, these tools can detect scam patterns early and warn users before they interact with dangerous contracts.
If users or wallets had integrated real-time chain retrieval systems, they might have:
-
Detected suspicious contract activity instantly, allowing them to stop interaction before losses occurred
-
Blocked the approvals before the transfer executed
-
Identified the scam by linking it to previous malicious campaigns
-
Reported the attacker’s address to exchanges and wallet providers for rapid action
Because chain retrieval solutions track common scam behavior across the blockchain — such as wallet-draining permissions, contract impersonation, and unusually fast token movements — they can quickly blacklist bad actors and alert the crypto community.
Moreover, many phishing contracts reuse tactics or even share similar code. This repetition makes them easier to flag through pattern recognition. In turn, chain retrieval tech scans for these signals and warns users before it’s too late.
Phishing attacks like this often rely on:
-
Slightly altered domain names
-
High-pressure prompts to connect wallets
-
Interfaces that mimic trusted apps down to the pixel
When users activate chain retrieval features, they can receive on-screen warnings such as:
-
“This contract has been flagged as malicious”
-
“You’re approving a high-risk transaction”
-
“This dApp has suspicious behavior history”
As a result, Web3 security tools are now integrating these alerts into wallet extensions, browser plugins, and DeFi dashboards. However, because adoption remains limited, scammers still find opportunities to exploit vulnerable users.
 Peckshield
Peckshield
Aave Community Urged to Stay Alert and Use On-Chain Tools
Currently, the Aave team is actively investigating the attack and has issued a public warning to its community. Specifically, they encourage users to:
-
Only access Aave through the official site
-
Avoid clicking links in social media comments or ads
-
Check URLs carefully for typos or subtle changes
-
Use wallets that include chain retrieval alerts and smart contract scanning features
As phishing attacks grow more sophisticated, the security practices of Web3 users must evolve as well. Aave’s situation proves that even the largest DeFi platforms remain vulnerable, and protecting your funds begins with vigilance combined with the right tools.
Consequently, Web3 security experts recommend that all crypto users — especially those interacting with DeFi platforms — integrate chain retrieval tools into their daily operations. Not only can these tools detect suspicious activity, but they also enable communities to share and block known scam addresses across multiple platforms.

