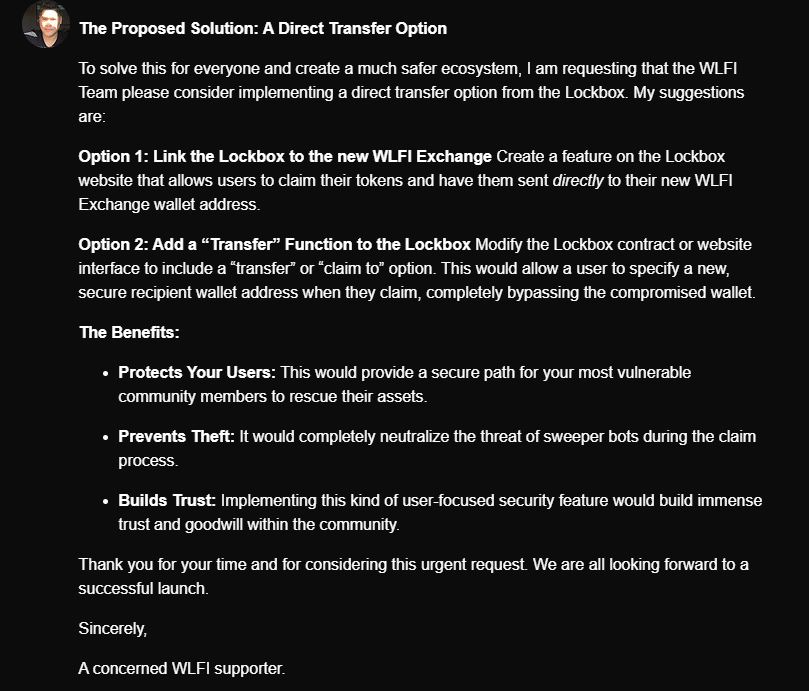
The crypto space is once again under fire, and this time the spotlight is on a vulnerability linked to EIP-7702 exploit. Hackers are using the loophole to steal WLFI tokens, targeting unsuspecting holders and draining wallets in seconds.
The attack is quickly spreading across the Ethereum ecosystem, raising questions about the risks of rushed proposals and how malicious actors are evolving faster than security measures.
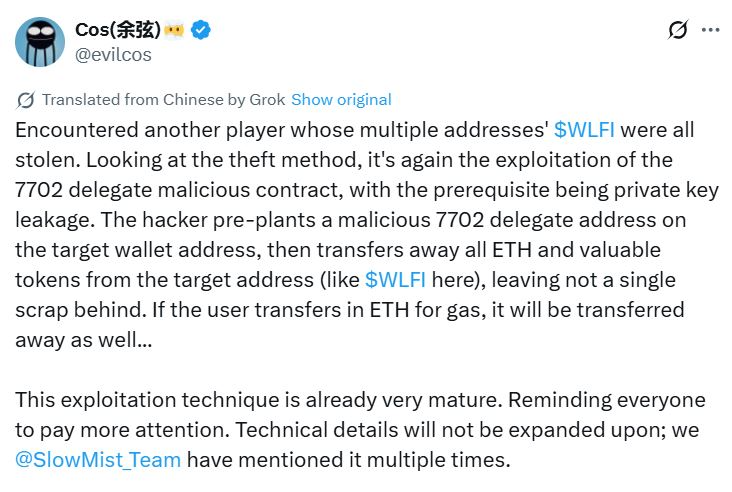
What is the EIP-7702 exploit
For those new to the story, EIP-7702 was introduced as an Ethereum Improvement Proposal that aimed to refine transaction efficiency and expand wallet functionalities. But as with many innovations in crypto, what was designed to improve usability ended up creating an unexpected attack vector.
Hackers discovered that the standard could be manipulated in a “classic” way, meaning the exploit leverages known transaction approval weaknesses that give attackers access to user funds. Once a wallet interacts with a malicious contract, permissions are silently granted, and WLFI tokens are instantly transferred out.
Cybersecurity firms tracking the event describe it as a “stealth drain”, where victims often don’t even realize what happened until their balance hits zero.
The EIP-7702 exploit is especially dangerous because it doesn’t require complex social engineering. Just one wrong click on a phishing link or interaction with a malicious dApp can hand over complete control.
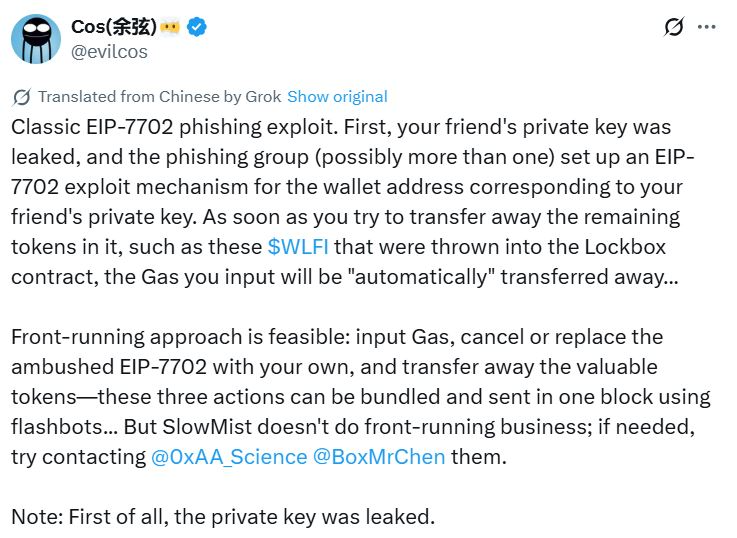
WLFI holders under heavy attack
The biggest casualty so far has been WLFI token holders. WLFI, a fast-growing DeFi project, has seen thousands of wallets compromised in just days. Several reports claim that the attackers are moving stolen funds through mixers, making it nearly impossible to trace.
On-chain data suggests that over 3 million WLFI tokens may already have been drained, though the real numbers could be higher since not all victims report their losses publicly.
Developers behind WLFI are urging holders to revoke token approvals and check their wallets immediately. Tools like Revoke.cash are being recommended to strip permissions that may have been unknowingly granted.
Meanwhile, Ethereum’s core developers are facing criticism for not anticipating this vulnerability when pushing the EIP forward. Many in the community now argue that security audits should be mandatory for any proposal that touches wallet-level approvals.
Security experts also warn that WLFI may not be the only target. Since the exploit lies within the EIP-7702 logic, any token operating with similar permissions could be next. This raises alarm bells across the wider DeFi ecosystem, especially for projects handling large amounts of liquidity.
How users can protect themselves
-
Avoid clicking unknown links or interacting with unverified dApps
-
Revoke any suspicious token approvals immediately
-
Move WLFI and other tokens to cold storage until a patch is confirmed
-
Monitor official WLFI and Ethereum channels for updates
The EIP-7702 exploit serves as yet another reminder of the fragile balance between innovation and security in crypto. As the industry keeps moving at lightning speed, every new proposal is both an opportunity and a potential risk. For WLFI holders, vigilance is no longer optional—it’s survival.